Embedded LDAP in 2 minutes (… and a bit of RBAC)
Embedded LDAP in 2 minutes
Running a standalone LDAP server is rather easy.
Getting that server to be embedded in your server may be slightly different.
ApacheDS has quite a few links to do it properly, but you need to do some gymnastics to compile the war file, set it up, start the server and finally get it working with different domains.
As part of the migration of Tempo to github, we also got the ApacheDS code in its own github fork.
So, all you need to do to get your embedded LDAP server, is to get your own war file, download tomcat and start the server.
You can setup additional LDAP partitions on the fly by editing the partitions.json file present in the expanded war file. No need to code. A partition looks like this:
“intalio”: {
“dn”:”dc=intalio,dc=com”,
“attributes”: {
“dc”:”intalio”,
“objectClass”:[“top”,”domain”,”extensibleObject”]
}
}
So you can add/remove then before starting the server, the applications filters will handle the initialization.
On the same note, ldif files to be imported can just be dropped in the classes folder, and they will be imported when the server start.
Import LDIF
Same again, drag and drop no need to code.
Hugues being still busy writing a wicked RBAC visual editor for Intalio|Designer to make it easy to manage the users and roles, we will rely on Apache Directory Studio (download, eclipse update).
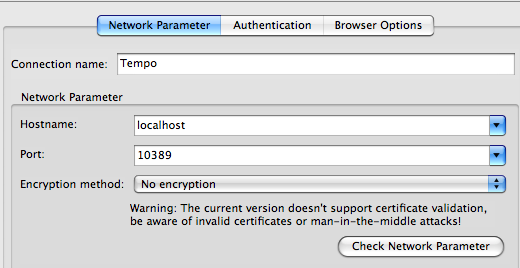
Network Parameters
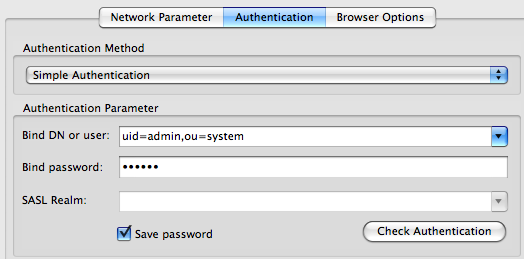
Authentication Settings
User is uid=admin,ou=system Password is secret by default, and you’re all set to connect.
Expanding the default, we can see:
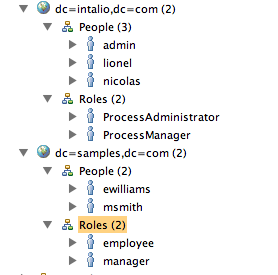
People and Roles
Copy and paste users, and roles, rename then on the fly, like here:
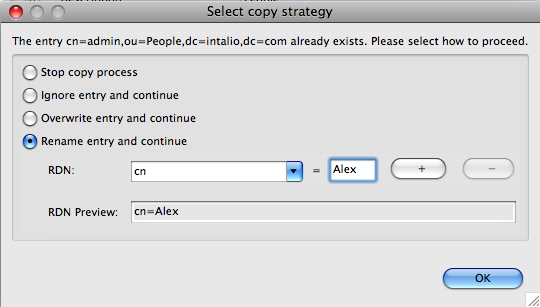
Create a new user
In Preferences, LDAP-> Entry Editor, remove the noisy LDAP attributes:
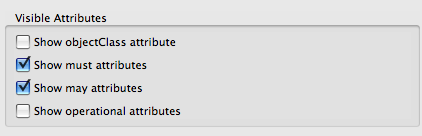
No noise
And use the entry editor, to edit the newly user:
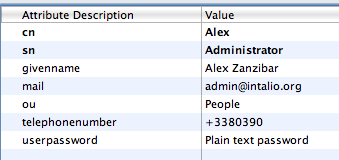
Edit User
Still a few glinches of LDAP prose, but we have written no code, we’re under 2 minutes and you should have an LDAP server setup.
… and a bit of RBAC
If you have Intalio|BPMS, (or the open source Tempo bundle) then LDAP authentication is either enabled by default or you can do that through the securityConfig.xml file:
<!– <bean id=”securityProvider” class=”org.intalio.tempo.security.simple.SimpleSecurityProvider” init-method=”init”>
<property name=”configFile”>
<value>${org.intalio.tempo.configDirectory}/security.xml</value>
</property>
</bean> –><bean id=”securityProvider” class=”org.intalio.tempo.security.ldap.LDAPSecurityProvider”>
<property name=”propertiesFile”>
<value>${org.intalio.tempo.configDirectory}/ldap.properties</value>
</property>
</bean>
Then, head to the local integrated RBAC Query Service, and try to see which users for which roles:
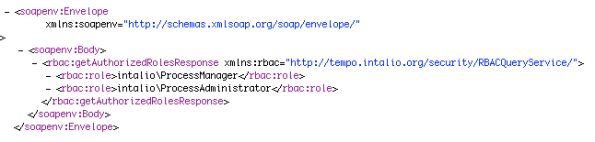
Soap me
Voila !